Presented by Dynamic Internet Technology Inc., Oct. 2nd, 2002
On Sept. 28th, reports came from China that visits to dissident websitess were being redirected to different IPs. Analysis shows that this is an unprecedented large-scale domain name hi-jacking in China achieved through DNS record spoofing. This effort is the result of an escalated level of Internet censorship in China.
0. The discovery
In Hong Kong, there were reports of people seeing the Falun Gong website www.minghui.org or news sites disliked by Chinese authorities, like dajiyuan.com, upon visiting unrelated websites. In Mainland China, users who used to be able to visit DynaWeb cannot now - users who try to visit other dissident sites still get "server not found" errors. Careful users have
found out, however, that their computers were actually trying to connect to the incorrect IP and then failing to find a server for that IP.
When a user visit a website with a domain name, by default, the user’s ISP's DNS server will be queried first to find out the IP of that site. An IP address is similar to the address of a house;
it is what the Internet uses to locate computers so as to send them information. All Internet traffic deals with IP addresses.
website defacement can be achieved through either modifying a web page on a server or by modifying the DNS record so that a user will never reach the correct website. The observations reported on Sept. 28th are known
as DNS spoofing.
Further investigation and analysis will most likely reveal this to be part of a new development of Internet censorship in China.
1. Who is targeted by the Domain Name Hijackings at this time and how?
1.1 Testing methodology
In July, DynaWeb (DIT Inc.’s secure proxy network for Chinese users to access blacklisted URLs) published its Top Ten Forbidden Websites that are visited through DynaWeb. They are:
www.renminbao.com
www.dajiyuan.com
www.bignews.org
www.creaders.com
www.rfa.org
www.internetfreedom.org
www.voanews.com
www.minghui.org
www.kanzhongguo.com
www.peacehall.com
Under a Windows 2000 computer, the following command will query the targeted DNS server and domain name to see if the correct IP is returned:
C:\> Nslookup [domain name] [domain name or IP of targeted DNS server]
A list of more than 50 DNS servers from various local ISPs in China were used for testing, including servers in Hong Kong and Macau. The locations cover the most densely populated provinces and cities.
1.2. Test 1: scale of the spoofing
On Sept. 30th when testing was performed on the top ten forbidden websites and the DNS server list we have, all of these ten sites resolved to the same IP address on all DNS servers on the list, except in Hong Kong and Macau. The IP is 64.33.88.161, or http://falundafa.ca - a Canadian registered non-profit organization aimed at promoting the practice of Falun Gong.
Many DynaWeb domains were pointed to 64.33.88.161 by the DNS servers. In fact, all DNS servers that
were tested, except the ones from Hong Kong and Macau, pointed to this IP address when they queried DynaWeb domains.
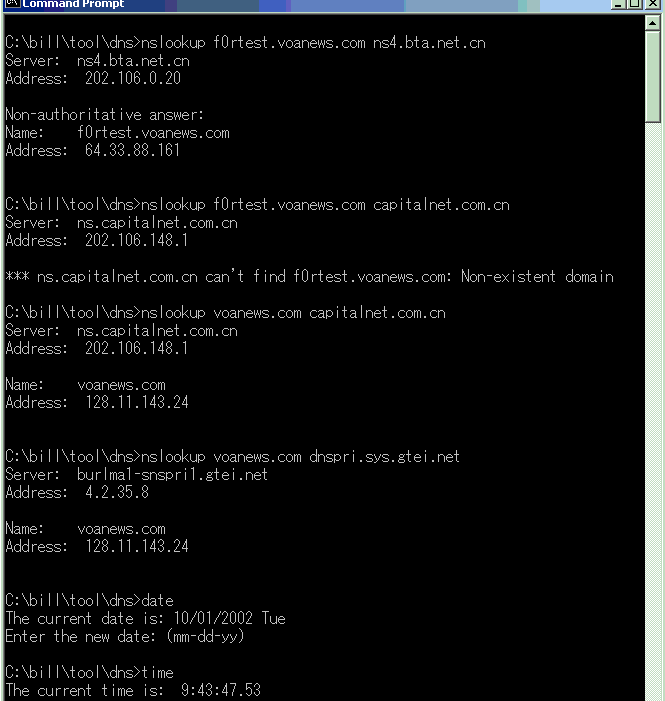
1.3. Test2: Extent of the spoofing besides the default www subdomain
The DNS servers were queried with a non-existent subdomain of the effected domains. See Fig. 1 output for “nslookup f0rtest.voanews.com ns4.bta.net.cn”. A "Non-authoritive answer" of 64.33.88.161 is returned, which claims that it is retrieved from some other DNS server. On Oct. 1st, when capitalnet.com.cn was queried, it returned correctly that the
address f0rtest.voanews.com doesn’t exist. (Fig. 1).
These tests with f0rtest.voanews.com show that the whole domain name space of voanews.com is spoofed to 64.33.88.161. If websites less reputable then
voanews.com are spoofed like this, it will be a classical case of web defacement.

1.4. Test 3: Extent of the spoofing – alternative domain names
Both dajiyuan.com and epochtimes.com domains are spoofed. (Fig. 3) All variations of
Tibetan sites are spoofed: www.tibet.net, www.tibet.com,
www.tibet.org, www.tibet.ca .
1.5. Test 4: Extent of the spoofing – string filtering
If there is “minghui” anywhere in the URL string, the DNS server will return 64.33.88.161. (minghui.org is the official website of Falun Gong.) Even the bogus web URL “aminghuib.test” is spoofed!
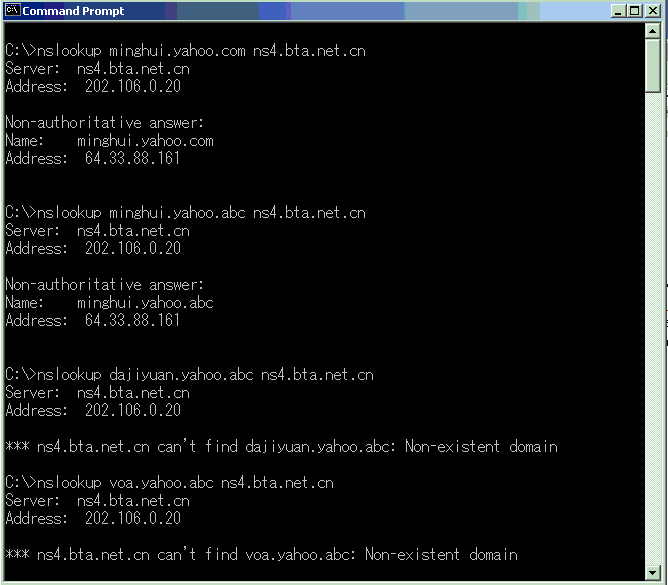
The keywords “voa”, “dajiyuan”, and “Tibet” do not experience the same problem.
1.6. Source of the spoofing
Since no DNS spoofings have been reported outside of China on these popular sites, this newly discovered DNS spoofing of some 50+ DNS servers on Sept. 30th is more likely a result from operations on those computer themselves, or some other DNS servers in China they always query.
The filtering of the term “minghui” could be performed by additional programs on all DNS servers or at any other level of China's packet filtering firewall.
It is interesting to notice that capitalnet.com.cn returned the incorrect IP on Sep. 30th, and then returned the correct IP on Oct. 1st. This has to be the result of intentional operations as well. It will be interesting to see if more DNS servers return to normal.
2. Who is the beneficiary and who will lose?
2.1 Falundafa.ca
Falundafa.ca won’t benefit from these redirections. It is already blocked in
Mainland China beginning from 1999 when China launched its campaign against Falun Gong.
2.2 People to benefit will be those people who hate some or all of the forbidden websites.
2.2.1 DynaWeb
Since DynaWeb has been providing secure access to blocked sites for Chinese
users, spoofing DynaWeb domain names will benefit those who hate those dissident websites.
2.2.2 Other forbidden sites
At first look, nobody benefits from DNS spoofing forbidden news sites that are already blocked. Moreover, users are redirected to another blocked IP, so users in China won't see any difference. The IP 64.33.88.161 (falundafa.ca)
won't benefit from
this - none of the spoofed sites will benefit from it.
In the long run, this trick will actually block those sites forever effectively. Once in a
while, a forbidden site will change their ISP and have a different IP. This in effect gets around the IP blockage in China. By pointing all DNS records of
those domain names to the same IP, those sites will always be blocked even if they change ISPs (and
obtain a new IP).
Therefore, Chinese users who are eager to see the previously mentioned forbidden sites or any forbidden sites will lose from this DNS spoofing.
2.2.3 Sina
While dailynews.sina.com.cn is pointed to 64.33.88.161 (which is falundafa.ca), sina and those who try to visit sina lose since users cannot visit the site. Some users in Hong Kong will see the Falun Gong site since their DNS server is affected (as long as they are not blocked from accessing Falun Gong sites). This redirection will force users to read those sites forbidden in Mainland China. It is definitely not a good promotion for the forbidden sites
to force everyone to visit them! This whole fiasco won’t benefit anybody. More analysis about sina will be performed in later sections.
3. How much effort does this DNS hijacking requre, and what
does this reveal?
The selection of targets: These targets are an authoritive list of what the Chinese government dislikes or what they dislike most.
Technical effort: More than 50 DNS servers of different local ISPs all over China were checked and all were found to be part of the hijacking. We can infer that all ISPs in China
are affected. For hackers, it is a huge effort. For the Chinese authorities, it is easy and more of a decision to make and implement it through a
centralized system.
Moreover, the string filtering of “minghui” illustrates how much the responsible party hates Falun Gong. This technology is beyond DNS spoofing in the common sense or found
in hacker literature. The selection of “minghui” shows the attention this super hacker pays to Falun Gong, and these
kinds of details regarding the DNS hijackings all seem to indicate the
Chinese Government.
Compared to the effort put into this new wave of website blocking, dailynews.sina.com.cn’s being redirected to 64.33.88.161 is minor. It is likely to be a minor mistake some Internet police made unintentionally, or
perhaps they did it on purpose.
4. Further work
The filtering mechanism used for filtering the word “minghui” is not clear. It will be helpful to have multiple computers in China query DNS servers outside of China. This will demonstrate if there is filtering and spoofing of DNS queries by the firewall in China.
At least one DNS server is found to be functioning normally as of Oct. 1st. It will be interesting to follow up to see if more DNS servers will stop returning incorrect IPs.
5. Conclusion
Starting Sep. 28th or earlier, a national DNS spoofing campaign was launched from China against websites by the Chinese government. DNS query string filtering was implemented to target a Falun Gong website,
www.minghui.org.
Dynamic Internet Technology Inc. will follow up with more research on this new wave of Internet censorship.